Discover like a pro
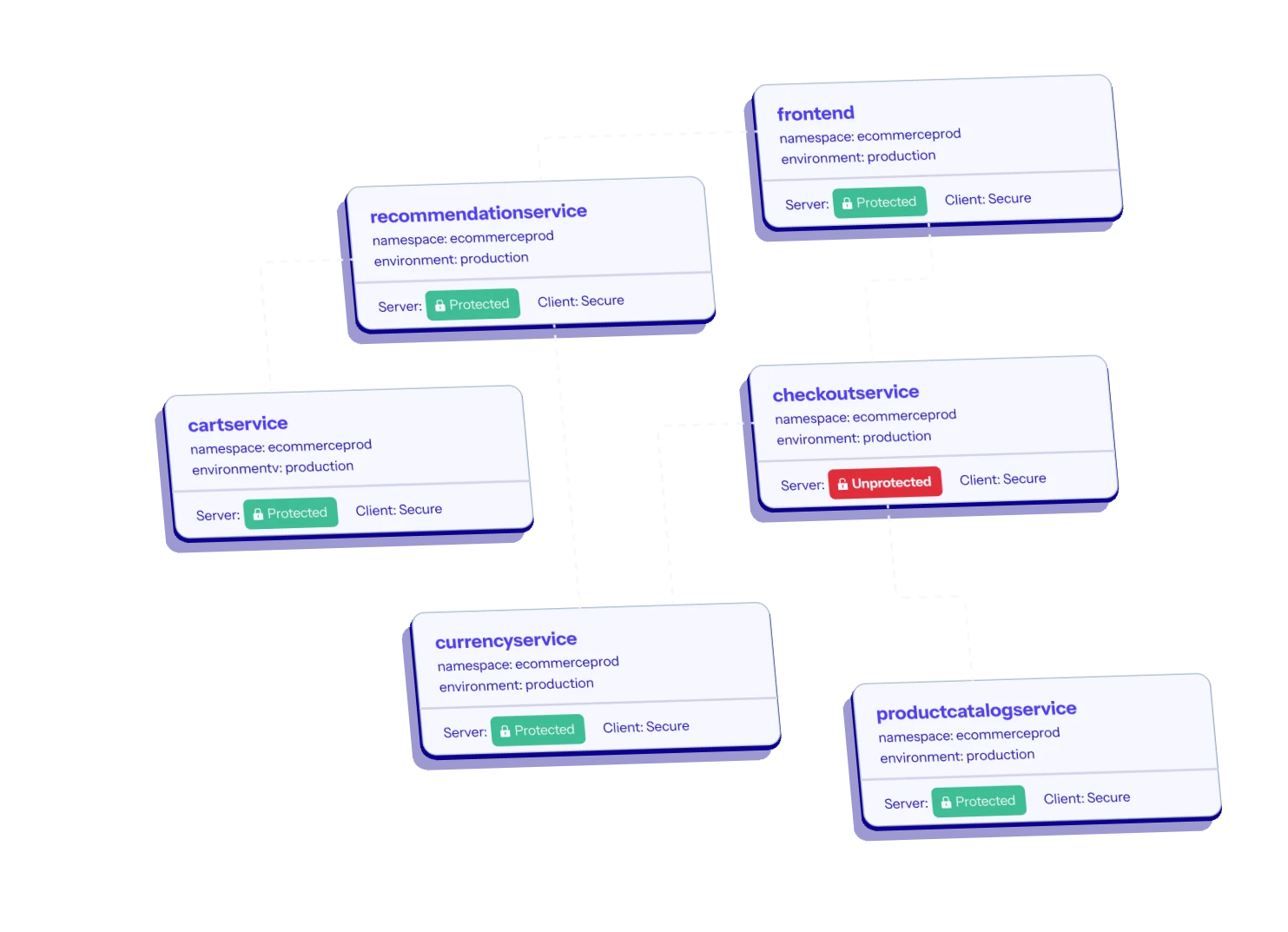
No more hunting for security gaps! Otterize makes it a breeze to find sensitive services in your Kubernetes cluster. Map clusters and zero in on where you need that extra layer of protection, all without breaking a sweat.
🚨 KubeCon + CloudNativeCon Announcement:
Otterize Unveils Support for Microsoft Azure IAM, Google Cloud IAM, and Introduces Blast Radius & Compliance Mapping →


Say goodbye to wrestling with AWS IAM, Azure IAM, Google Cloud IAM, network policies, and database access. Just tell us what your services need to call, and let Otterize handle the rest. Simplify your infrastructure, on your terms!
No more hunting for security gaps! Otterize makes it a breeze to find sensitive services in your Kubernetes cluster. Map clusters and zero in on where you need that extra layer of protection, all without breaking a sweat.

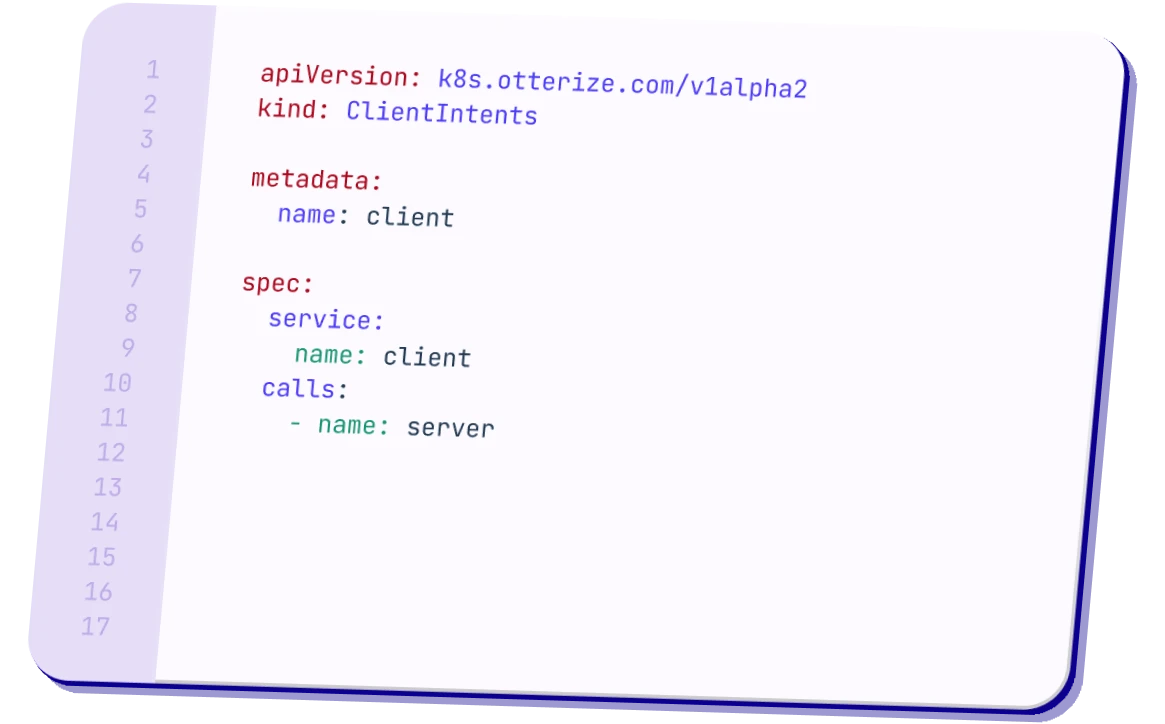
Say goodbye to security stress! Otterize is your trusty sidekick that takes the heavy lifting off your plate. It automatically generates zero-trust policies based on your app's needs, securing your services effortlessly.
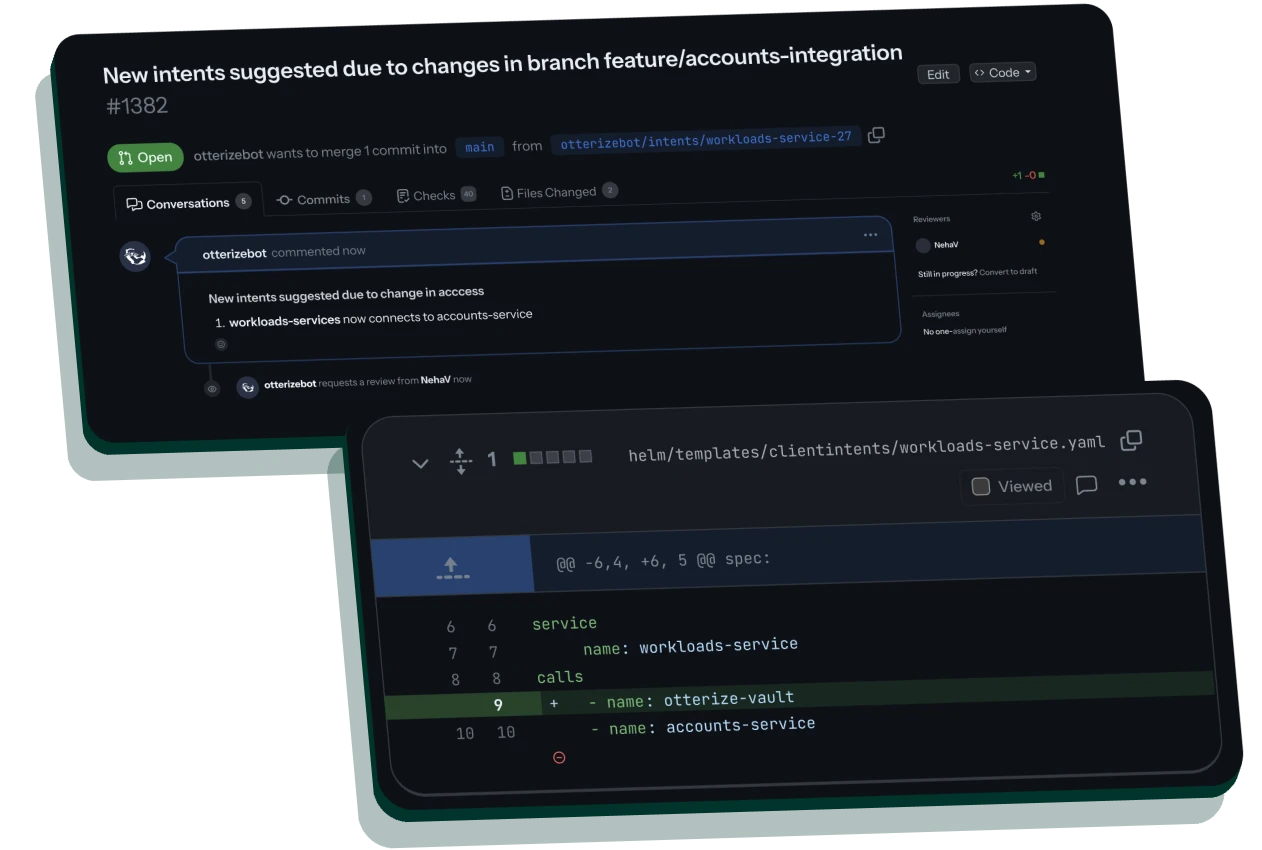
As your digital kingdom grows, so does your security, thanks to Otterize. Scaling up is a walk in the park. Safeguard more services and teams smoothly with automatic pull requests—it's security made simple!
The second episode of First Person Platform, a podcast: platform engineers nerd out with Ori Shoshan on access controls, Kubernetes, and platform engineering.
We explore the limitations of relying solely on Kubernetes network policies as a solution for achieving zero-trust between pods, identifying multiple flaws that hinder their effectiveness in meeting the demands of real-world use cases, particularly when prioritizing developer experience in a Kubernetes-based platform.
The first episode of First Person Platform, a podcast: platform engineers nerd out with Ori Shoshan on access controls, Kubernetes, and platform engineering.