Security isn’t just about building walls; it’s about
building trust.
That’s why we’ve taken a leap towards transparency by making Otterize open source.
We believe in security for all
Transparency, innovation, and trust are at the core of our mission. Join us in shaping a safer digital future, together. Explore, contribute, and strengthen security with Otterize.
Transparency builds trust
See the code, trust the code. Our open source approach ensures transparency and accountability.
Constant evolution
Security never stands still. By going open source, Otterize stays on the cutting edge of protection. Join us in shaping the future of security.
Community-powered innovation
Collaboration fuels innovation. With open source, we invite you to join our community and share ideas, and build a secure digital world together.
What are you waiting for? Experience the power of Otterize OSS for yourself
Simplify network policy management
Why make things complicated when they can be simple? At Otterize, we’re all about making your life easier.
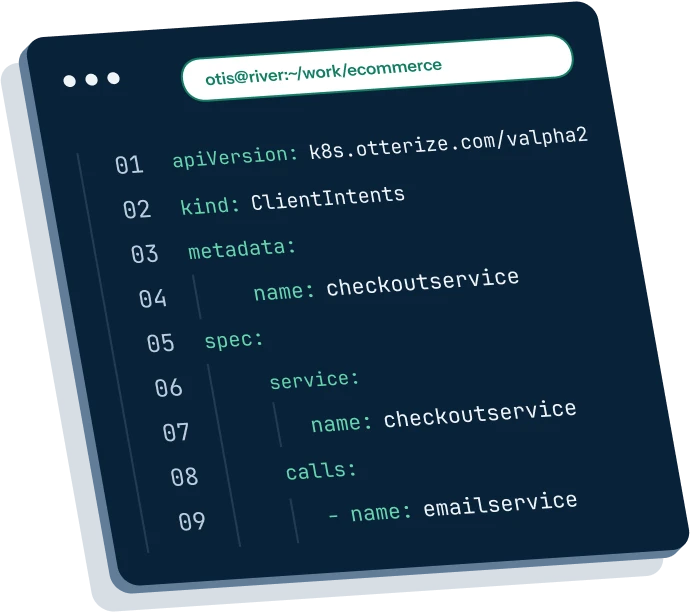
Client intents: your new best friend
Forget the hassle of managing pod identities and labels or diving deep into network policy configurations. Say hello to client intents—the easy way to set access controls.
Bootstrap with ease
Starting from scratch? No worries! Bootstrap client intents effortlessly by using network mapper to learn from existing traffic patterns.
Resource Library
Read blogs by Otis, run self-paced labs that teach you how to use Otterize in your browser, or read mentions of Otterize in the media.
- Kubernetes
New year, new features
We have some exciting announcements for the new year! New features for both security and platform teams, usability improvements, performance improvements, and more! All of the features that have been introduced recently, in one digest.
- Kubernetes
First Person Platform E04 - Ian Evans on security as an enabler for financial institutions
The fourth episode of First Person Platform, a podcast: platform engineers and security practitioners nerd out with Ori Shoshan on access controls, Kubernetes, and platform engineering.