Discover like a pro
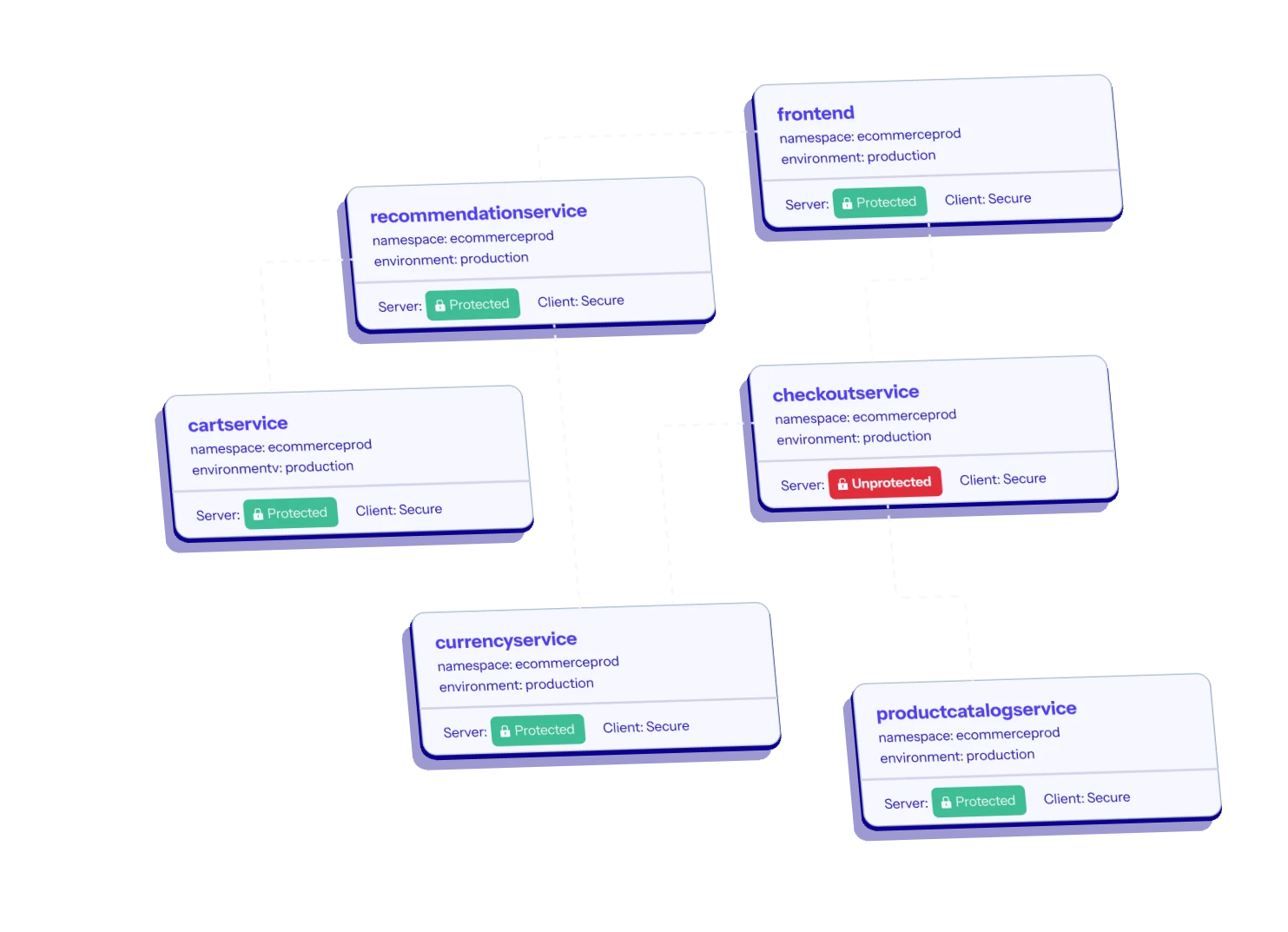
No more hunting for security gaps! Otterize makes it a breeze to find sensitive services in your Kubernetes cluster. Map clusters and zero in on where you need that extra layer of protection, all without breaking a sweat.
🌎 OTTER THIS WORLD:
How to chart Kubernetes egress traffic with Otterize →



Say goodbye to wrestling with AWS IAM, Azure IAM, Google Cloud IAM, network policies, and database access. Just tell us what your services need to call, and let Otterize handle the rest. Simplify your infrastructure, on your terms!
No more hunting for security gaps! Otterize makes it a breeze to find sensitive services in your Kubernetes cluster. Map clusters and zero in on where you need that extra layer of protection, all without breaking a sweat.

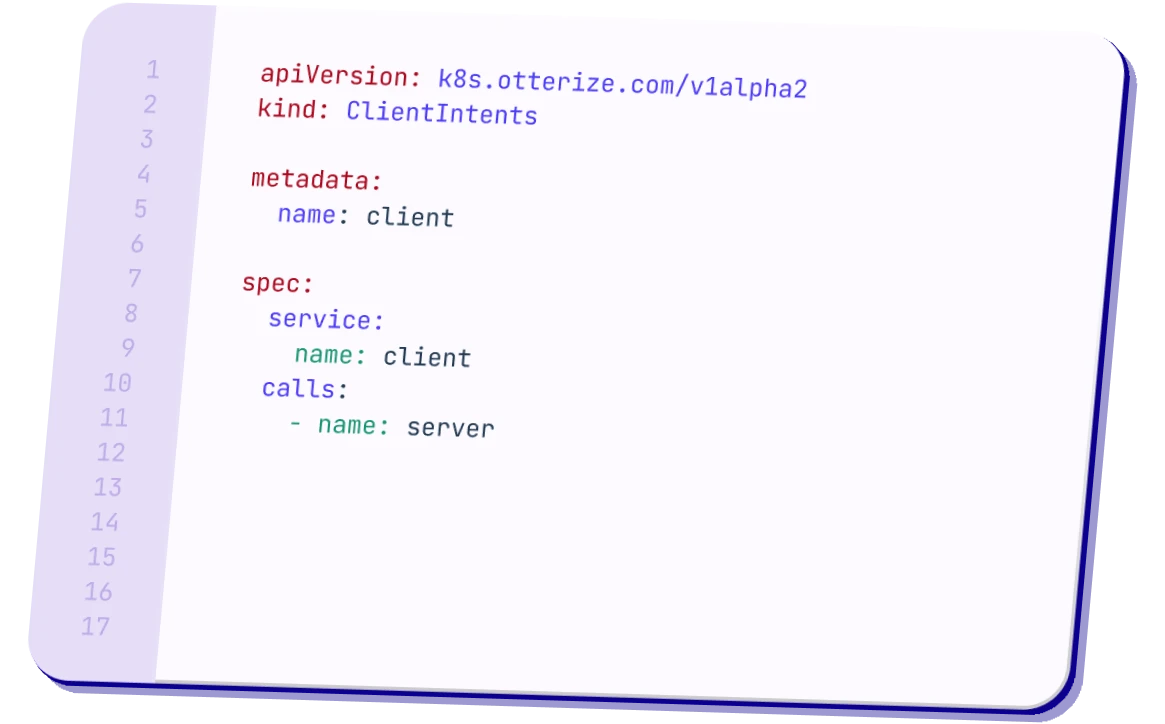
Say goodbye to security stress! Otterize is your trusty sidekick that takes the heavy lifting off your plate. It automatically generates zero-trust policies based on your app's needs, securing your services effortlessly.
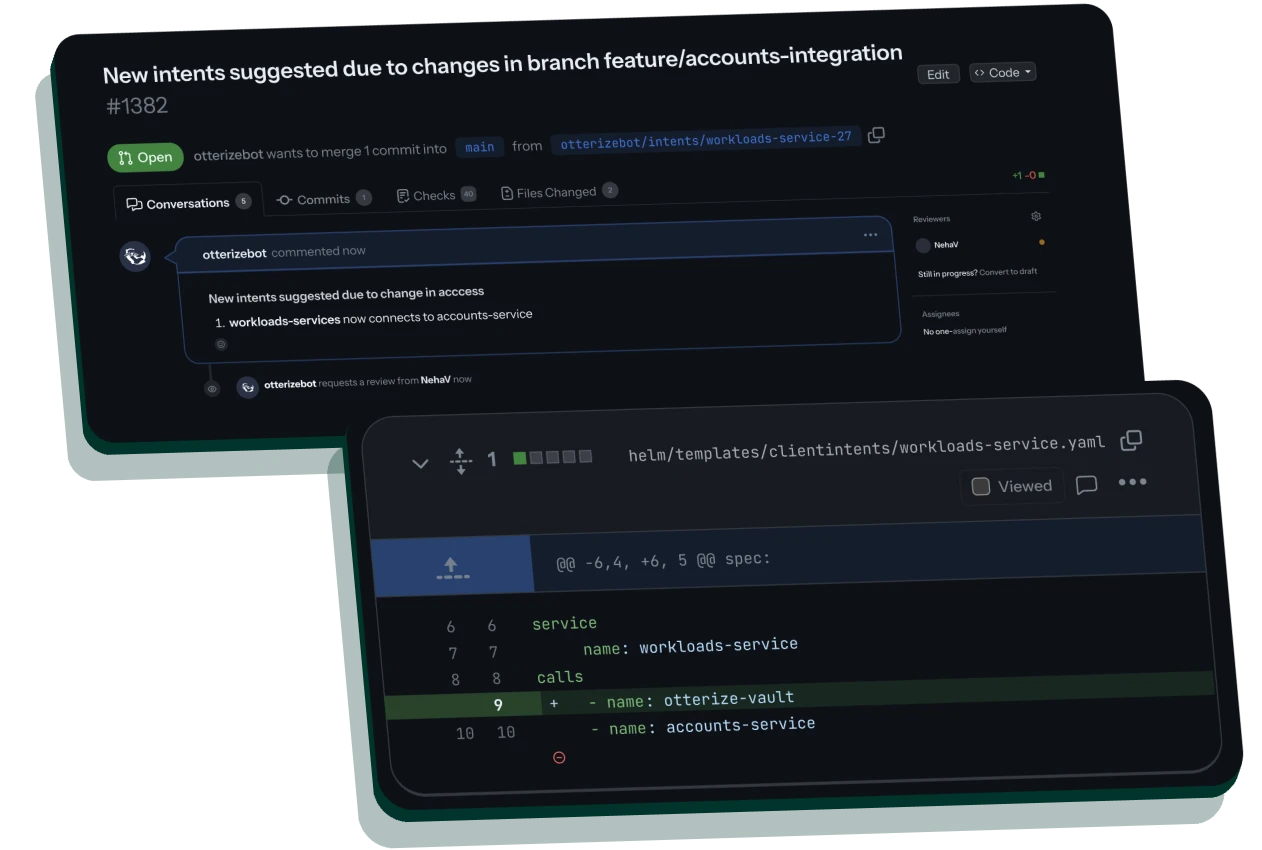
As your digital kingdom grows, so does your security, thanks to Otterize. Scaling up is a walk in the park. Safeguard more services and teams smoothly with automatic pull requests—it's security made simple!
Discover how Otterize helps you gain visibility into your egress Kubernetes connections.
Learn Istio fundamentals for authorization policies and request authentication, and how Otterize automates application security and zero-trust.
Discover how to automate zero-trust IAM security for EKS applications and AWS resources using AWS Controllers for Kubernetes (ACK) and Otterize.